- October 11, 2025


I’ve built a new free tool for the technical SEO community: the SEO Security Header Checker. It’s designed for a specific job; to audit key HTTP headers across any number of URLs, fast. No logins, no fluff, no third-party API calls. You paste in a list of URLs, and it tells you whether the security headers you care about are present. That’s it.
There’s a lot of noise in the SEO tool landscape. Some tools look impressive, but underneath they’re just giving you rehashed surface-level data or repeating Lighthouse output. This one’s different.
The SEO Security Header Checker is built for a specific, technical use case. It lets you bulk-audit any number of URLs for the presence of key security headers. These aren’t just compliance boxes. Some of them actively shape how bots, browsers, and platforms behave on your site. They can impact indexing, crawling behaviour, visibility in embedded contexts, and even how well your analytics work. The reason for me creating this tool is because all the other free tools out there limit you to a single URL at a time, which is fine for a handful of checks. But, in bulk I needed more options, so I vibe-coded this tool.
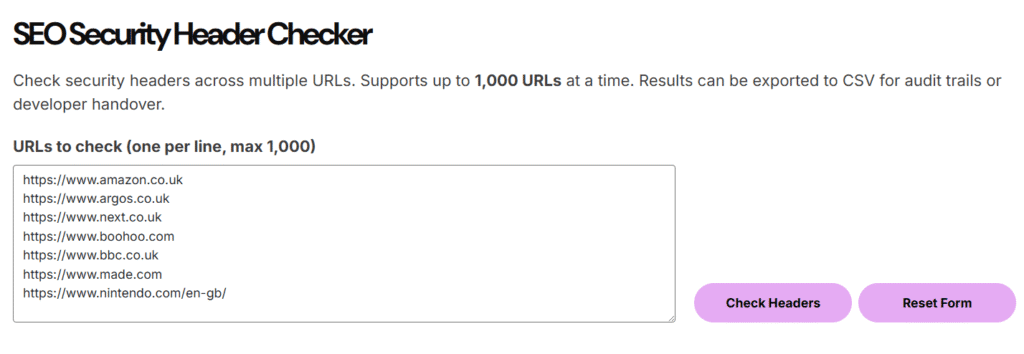
This tool is free, fast, browser-based, and runs without sending your data to third-party APIs. It does one job well: check whether your URLs return the right server-side headers, in bulk, and export the results cleanly.
Security headers exist to give instructions to browsers and bots. Some prevent risky behaviours, others enforce secure protocols or control visibility. From an SEO perspective, the headers we care about can affect:
Here’s what can go wrong in the wild:
Most of these do not get flagged in crawls or automated SEO audits. You only catch them if you look at raw response headers. That’s where this tool comes in.
The tool currently checks for the presence (not values yet) of the following:
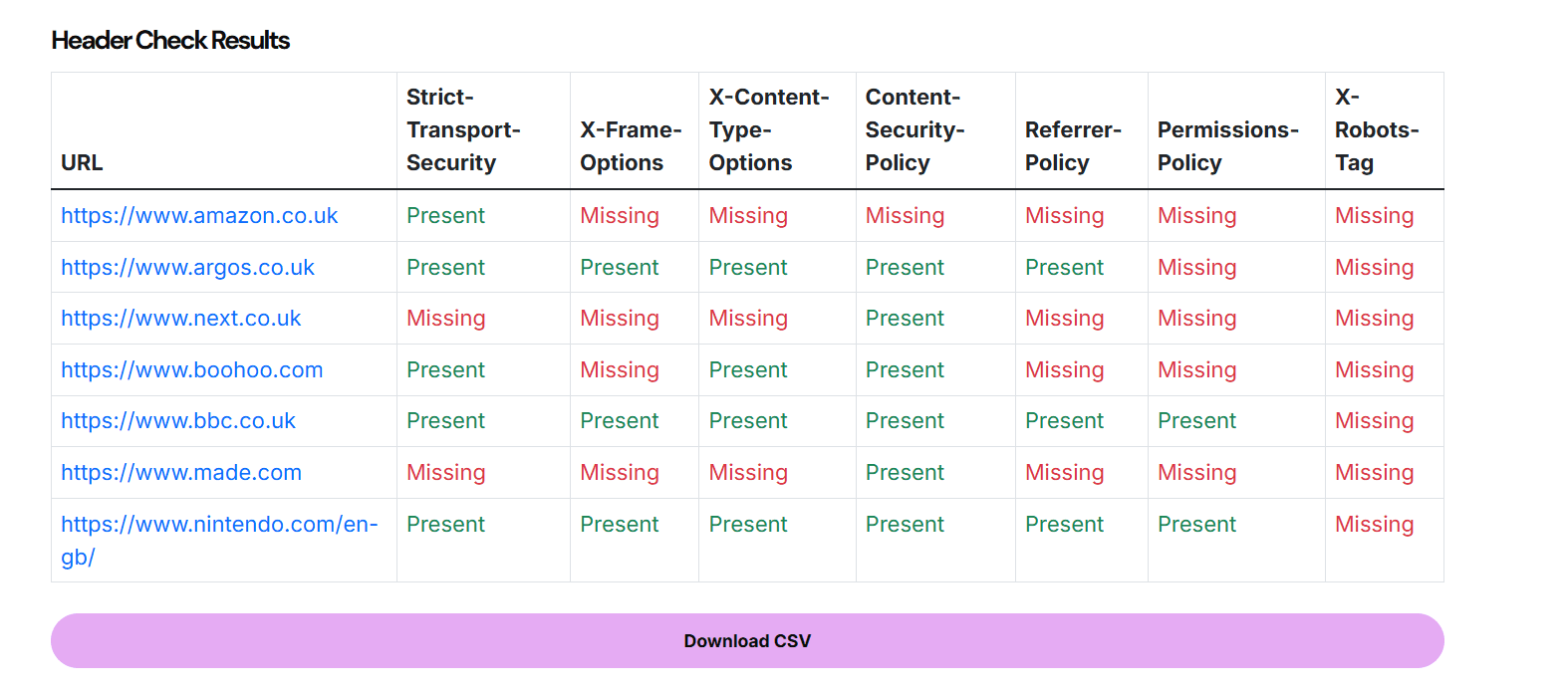
Each of these headers serves a different purpose, but collectively they tell you whether the server has been configured with basic hygiene in mind. The last one, X-Robots-Tag, is particularly relevant for SEO. It is often forgotten on PDF files, image folders, or gated content that still returns 200 OK.
If you’re a technical SEO working in:
Then this tool will save you time. It removes the need to manually open DevTools for each URL. You can paste in 10, 100, or up to 1,000 URLs and get a fast overview of which headers are present. You can then export to CSV, pass to your dev team, or use it as part of your audit evidence.
Here’s where it’s already proven useful for me:
Many clients host PDFs, whitepapers or downloadable resources. These don’t always need to be surfaced or indexed, but developers often forget to add X-Robots-Tag: noindex on non-HTML assets. This tool lets you bulk-test every asset directory quickly.
If you’re working on a site using Cloudflare, Akamai or another CDN, the headers might not be coming from origin. They could be injected at the edge. Use this tool to test specific URLs from your production CDN endpoint and verify what’s actually returned.
Dev teams ship fast. It’s common for security headers to get wiped in a new NGINX config or during container rebuilds. Paste in a set of high-value URLs and check if anything important has disappeared from the headers.
Sometimes you need to explain to stakeholders why a technical SEO task matters. Exporting a CSV with clear pass/fail visibility across headers gives you evidence to point to in training sessions, decks or documentation.
There’s also a Reset button so you can start again without reloading the page.
You’re not getting synthetic scores or abstracted metrics. You’re getting a direct check against the raw HTTP headers for each URL, with a clean UI and an instant CSV export.
There’s no JavaScript-based DOM inspection, no false positives from headless rendering. This is a raw, HTTP-level audit.
It also doesn’t hit third-party APIs, so your URLs stay local. All requests are handled server-side through PHP. That means it works on large input sets without rate limits (upto 1000 URLs per check).
There’s a gap in the SEO toolbox for technical checks that go deeper than what Lighthouse or browser-based crawlers surface. This tool fills that gap for headers.
If you’re working across client platforms, reviewing CDN configs, or doing pre-launch QA, it gives you a fast way to verify what headers are there, and what’s been forgotten. It’s free, exportable, and doesn’t rely on third-party APIs or logins.
You can try the tool here:
https://chrisleverseo.com/tools/seo-security-header-checker/
Feedback is welcome. If you’ve got ideas for improvement or edge cases I should account for, drop me a message or comment on the LinkedIn post I shared: https://www.linkedin.com/feed/update/urn:li:activity:7337563965301932032/
Comments: